Botnet Action
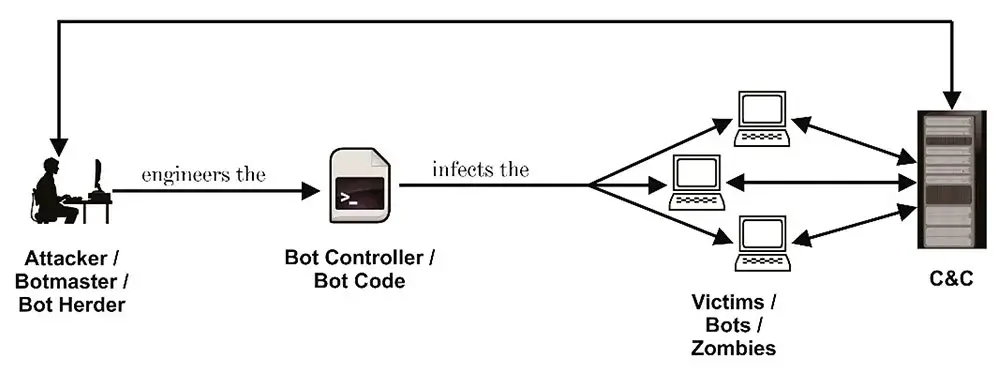
A botnet is a logical collection of Internet-connected devices, such as computers, smartphones or Internet of Things (IoT) devices whose security have been breached and control ceded to a third party. Each compromised device, known as a “bot,” is created when a device is penetrated by software from a malware (malicious software) distribution. The controller of a botnet is able to direct the activities of these compromised computers through communication channels formed by standards-based network protocols, such as IRC and Hypertext Transfer Protocol (HTTP).
How does a botnet attack work?
Once a cybercriminal (or bot herder) has control of a group of infected devices (composing a botnet) they can remotely command every device to simultaneously carry out coordinated activities, including malicious and criminal activities like:
DDoS Attacks: Distributed denial of service attacks leverage the number of devices in the botnet to send a massive amount of requests or payloads to overload a target server or website, rendering the service inaccessible to legitimate users. Even large companies like Sony and Electronic Arts have been victims of large-scale DDoS attacks caused by botnets, and could benefit from better DDoS protection services.
Spam Attacks: The majority of online spam attacks (email spam, comment section spam, form spam, etc.) are performed by botnets. Spam attacks are often used for spreading malware and phishing, and there are botnets that can launch tens of billions of spam messages per day.
Data Breach: Some botnets are specially designed to steal confidential and valuable information like banking details, credit card numbers, and so on. The ZeuS botnet , for example, is primarily designed to steal account information from various e-commerce, banking, and social media sites. Botnets may be designed to target very specific high-value services and digital assets in breaches and data leaks .
Monitoring: Compromised zombie devices will monitor the user’s activities and can scan passwords and financial information to report back to the bot herder.
Spreading the Botnet: A botnet will search for vulnerabilities in other devices, websites, and networks to spread the malware to other machines and grow the botnet, making the overall botnet attack worse.
How is a botnet created?
Botnets always consist of a command and control (C&C or C2) server and a group of zombie devices.
1. C&C Server
The bot herder runs a device (or a group of devices) that acts as a C&C server, which sends command programming to the zombie devices to drive their next activities. The bot herder may also rent the C&C server (or the commands) out to other parties. For example, a business can rent a C&C server and command a botnet to launch a DDoS attack on its competitors.
There are two different types of C&C servers:
Centralized: A centralized C&C server follows a client-server bot herding model, in which a single C&C server commands all the zombie devices in a centralized network. In some cases, additional C&C servers might be tasked as sub-herders between the main C&C server and the zombie devices, creating a proxy-based hierarchy, but all commands come from the main C&C server. The centralized model, allows the bot herder to be more easily discovered, and is thus considered obsolete/no longer ideal.
Decentralized: The more modern and preferred approach is the decentralized model, where all zombie devices can send and redirect commands to one another. The main C&C server only needs to contact one of the zombie devices to ensure the command gets relayed to the other zombies, which is why this model is also called a “peer-to-peer” model. The decentralized model protects the identity of the bot herder by making the C&C server more difficult to trace.
2. Zombie Devices
As discussed, zombie devices—often called bots—are devices that have been taken over by the bot herder as a part of the botnet, mainly due to malware infection. These devices, once compromised, will blindly follow the C&C server’s command.
While different bot herders might use varying techniques for “recruiting” new devices into the botnet, recruitment generally involves three core phases:
Phase 1: Finding and Exploiting Vulnerabilities
The first, and arguably the most crucial, step involves the attacker searching and finding vulnerabilities in a human user’s behavior—an application/software, a website, or any other potential inroad to a device. The objective of the attacker in phase 1 is to find ways to take control of a device, such as any vulnerability that can be exposed to a malware infection, for example.
For instance, the attacker might find vulnerabilities in a device user’s behavior that indicate malware could be successfully delivered to the user via a spam/phishing email. Or the attacker might notice an unpatched vulnerability on an application or an OS to exploit.
Phase 2: Actual Malware Infection
In this phase, the device is infected by malware and is now under the control of the bot herder.
Infection can happen in two different ways:
Passive: The infection happens without any help from human users. For example, when the infection happens due to an exploited software vulnerability.
Active: The infection happens after the human user takes a certain action, like downloading an email attachment or clicking a link on an already infected website.
Once infected, no matter what method was used, the device falls under the control of the attacker.
Phase 3: Taking Control of the Compromised Device
The third and final phase involves the bot herder organizing the infected devices into a network, the botnet, and performing the necessary configurations to ensure each of the infected devices can be remotely managed via the C&C server.
The bot herder will repeat these three phases with many devices to grow the botnet’s size. In some cases, botnets are able to grow to include millions of computers, smartphones, and IoT devices.
3. Most Concerning Botnet Attacks
While using a botnet to spread malware infections is a botnet attack by itself, botnets are more notably used to execute secondary cybercrime attacks, often on a very large scale due to the size of botnets.
While large-scale botnet attacks can come in various different forms, there are three vital types to protect your system/website against:
1. Phishing
Most botnets rely on spam and phishing tactics to infect more devices and grow the botnet in size.
In phishing and other forms of social engineering attacks, the botnet will send emails, post comments, and create messages on social media platforms imitating people and/or organizations that are known and trusted by the target victim.
As a botnet attack, phishing can be particularly difficult to defend against because no matter how advanced your security infrastructure is, it can totally crumble when just one employee or user in your network falls victim to a phishing attack. That’s why human error remains the top cause for successful data breach attacks and cybersecurity attacks.
2. Distributed Denial of Service (DDoS)
The idea behind using botnets for DDoS attacks is to overwhelm a target server with a massive number of requests (from the zombie devices) to crash, or at least slow down, the server significantly.
DDoS is one of the most common ways botnets are utilized in criminal attacks, and often the most dangerous. Damages resulting from DDoS attacks can be severe and long-lasting, not only in terms of financial damages, but also reputational damages.
It’s very important for any business that serves its customers online (which includes having a functional website) to have proper anti-DDoS measures and a functional anti-DDoS response plan. When a DDoS attack occurs, it is already too late to plan your response, so an actionable response plan must be prepared beforehand. Many businesses use a DDoS protection software to do this.
3. Account Takeover Attack
Bot herders can use botnets to perform various forms of Account Takeover (ATO) attacks, especially brute force (credential cracking) and credential stuffing attacks.
In a brute force attack, the zombie devices are commanded to try the different possibilities of a user password to “crack” the password. For example, if it’s a 4-digit pin, zombie device 1 will try “0000”, the second zombie device will try “0001”, and so on up to “9999” or until the right PIN has been guessed.
Defending against botnet ATO attacks can be quite challenging, and fairly effective in exploiting weak user credentials to take over accounts. Some businesses use an account takeover prevention software to minimize this risk.
With all that being said, there is quite a few ways to make money with a botnet. If you are into this type of thing then you already know where to look for the software and anything else needed. If you are not into this type of thing I guess just keep your passwords nice and strong, be careful who uses your computers, tablets and cell phones, and install some high end security software on any device you use.