Discord.io Hacked, 760K Users Data Stolen
The custom invite feature of Discord.io has been temporarily suspended due to a recent data breach that exposed the sensitive information of around 760,000 members.
Discord.io, while not affiliated with the official Discord platform, served as a third-party service enabling server administrators to generate customized invites for their chat channels. The majority of the community congregated on the service’s Discord server, which boasted an impressive membership of over 14,000 individuals.
Just yesterday, an individual going by the moniker ‘Akhirah’ initiated the sale of the pilfered Discord.io database on the newly established Breached hacking forums. As evidence of the breach, this threat actor disclosed four user records extracted from the compromised database.
For those who may not be acquainted with the re-emergence of Breached, it marks the revival of a notorious cybercriminal forum recognized for its illicit trade and disclosure of data obtained through various breaches.
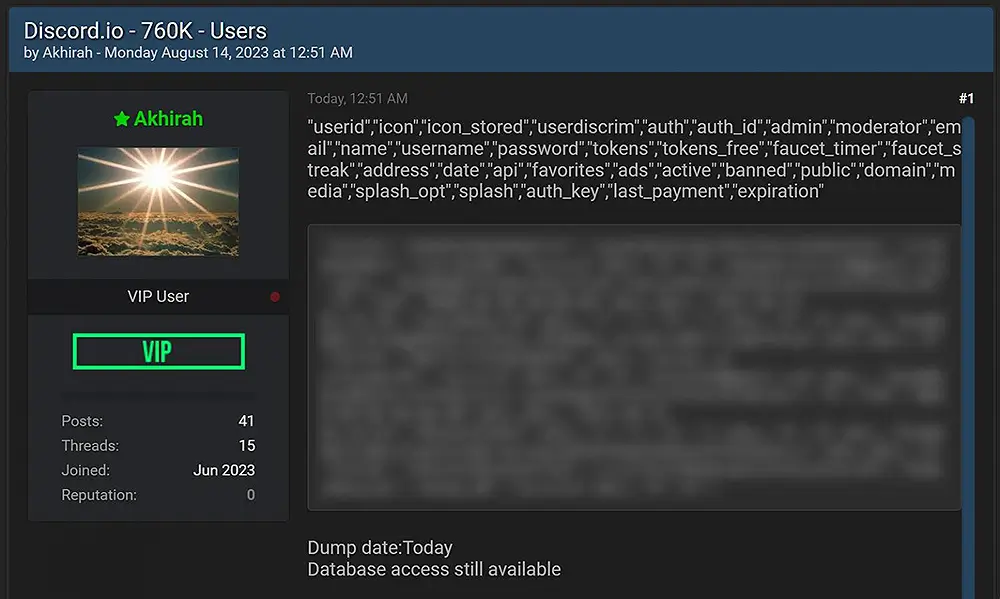
As per the claims made by the threat actor, the compromised database encompasses details pertaining to 760,000 users of Discord.io. This repository of information encompasses the subsequent categories of data:
"userid","icon","icon_stored","userdiscrim","auth","auth_id","admin","moderator","email","name","username","password","tokens","tokens_free","faucet_timer","faucet_streak","address","date","api","favorites","ads","active","banned","public","domain","media","splash_opt","splash","auth_key","last_payment","expiration"
The breach has exposed certain critical information about the affected members, encompassing their username, email address, billing address (a minority of individuals), salted and hashed password (a minority of individuals), as well as their Discord ID. Discord.io has clarified that while this data is not inherently confidential and can be accessed by anyone sharing a server with the user, its inclusion in the breach does introduce the potential for others to associate a Discord account with a specific email address.
In response to these events, Discord.io has officially acknowledged the breach’s authenticity through notifications on both its Discord server and website. Consequently, the platform has initiated the temporary suspension of its services.
A communication from the service’s Discord server reads, “Discord.io has experienced a data breach. We are halting all operations for the foreseeable future.” Additionally, a message on their website outlines their intention to share this message and more information on the breach in their designated “#breach-notification” channel, along with upcoming updates to their website to reflect these developments.
Discord.io’s website contains a timeline that chronicles their awareness of the breach, initially sparked by a post on a hacking forum. Following this, they substantiated the veracity of the leaked data and subsequently embarked on shutting down their services and discontinuing all paid memberships.
Despite these actions, Discord.io has not been in contact with the individual responsible for the breach and has refrained from divulging any details about the method used for the intrusion.
In a conversation with BleepingComputer, the seller of the Discord.io database, Akhirah, confirmed that no communication has taken place between them and the operators of Discord.io.
The Discord.io site acts as a directory where visitors can search for Discord servers matching specific content and obtain an invite to access it. In some cases, it is required to purchase and spend the site’s virtual currency, Discord.io Coins, to gain access to an invite.
When creating these Discord server profiles, the Discord.io terms of use say that all content is the member’s sole responsibility but that the operators have the right to remove any content that is illegal or breaks their rules.
From the limited archived pages of the site, BleepingComputer has seen Discord servers in the directory for a wide variety of interests, including anime, gaming, adult content, and more.
However, when BleepingComputer asked Akhirah about the sale of the database, they said it was not only about making money but about how Discord.io allegedly links to illegal and harmful content.
“It’s not just about money, some of the servers they overlook I talking about pedophilia and similar things, they should blacklist them and not allow them,” Akhirah told BleepingComputer.
The hacker told BleepingComputer that there has been a lot of interest in the database but mostly from people who want to use it for “doxing other people they have problems with.”
Instead, Akhirah says they would prefer to wait for the Discord.io operators to contact them about removing allegedly offensive material from the site in exchange for not selling or leaking the stolen database.
Although the hacker claims not to have sold the compromised database, it’s crucial for all members to exercise caution and approach the situation as if their data could be misused.
The breached passwords are secured through bcrypt, a hashing method known for its resource-intensive nature, rendering them resistant to swift decryption.
However, the email addresses within the breach hold value for potential threat actors, as they could facilitate targeted phishing campaigns aimed at acquiring more sensitive information.
Consequently, if you’re a member of Discord.io, it’s advisable to remain vigilant for any unusual emails that contain links directing you to pages requesting your password or other confidential details.
To stay informed about developments related to the breach, it’s recommended to regularly check the primary website. This source should provide updates on possible password resets or official communications from the service.